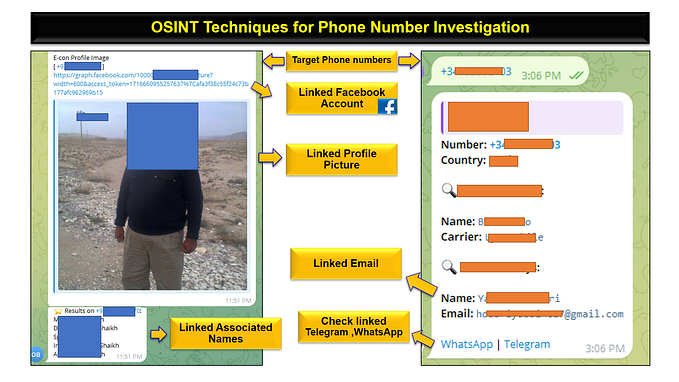
Member-only story
25,000$ Bounty — Simple SSRF Led to AWS Credentials Exposure
Exploiting SSRF in Analytics Reports to Gain AWS Access

Timeline
- 📅 Reported: November 23, 2023
- ✅ Fixed: November 24, 2023
- 💰 Bounty: $25,000
- Severity: Critical (9.8/10)
Introduction
Server Side Request Forgery (SSRF) is one of the most dangerous vulnerabilities in web applications, especially when it allows attackers to access internal services or cloud metadata endpoints.
Recently, a researcher found a critical SSRF vulnerability in an Analytics Reports feature that exposed AWS credentials, which could potentially allow full control over cloud services.
In this article, I’ll break down the vulnerability, how it was exploited, and how such attacks can be prevented.
What is SSRF?
Server Side Request Forgery (SSRF) happens when an attacker tricks a web server into making requests to internal services or external systems.
Types of SSRF Attacks:
- Basic SSRF — The attacker forces a server to make a request to an unintended destination.