Member-only story
Critical SQL Injection Exploit in URL Paths: Bounty Report
Exposing Critical Vulnerabilities: How a Simple SQL Injection Can Compromise Entire Databases

Introduction
A recent security report exposed a critical SQL Injection (SQLi) vulnerability within the URL path of an MTN Group web application. This vulnerability, discovered by security researcher @almuntadhar, could potentially allow attackers to gain unauthorized access to sensitive database information. Let’s break down the vulnerability, its impact, and how attackers can exploit such flaws.
Vulnerability Overview
- Vulnerability Type: SQL Injection in URL Paths
- Severity: Critical (9.0–10)
- Reported On: January 26, 2025
- Disclosed On: March 6, 2025
- Affected Platform: MTN Group
- Weakness Category: Improper Input Validation (SQL Injection)
Details of the Vulnerability
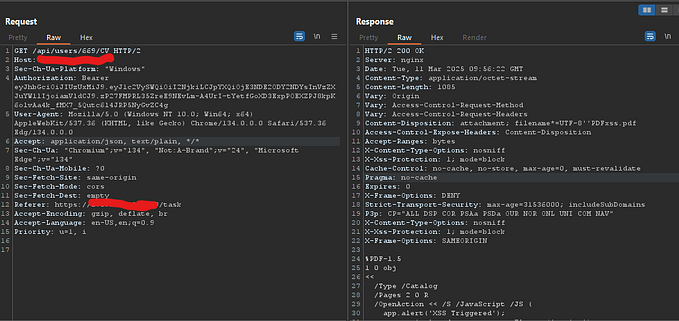
The vulnerability was found in the customerId parameter within the following URL path:
https://seesure.admyntec.co.za/customerInsurance/newCustomerStep5Pending/customerId/732562/contactPersonId/0/msisdn/