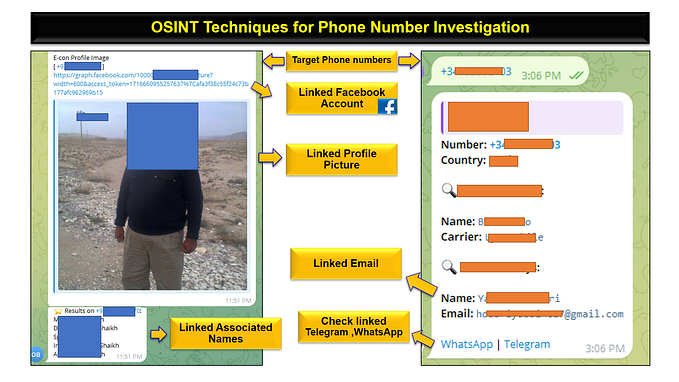
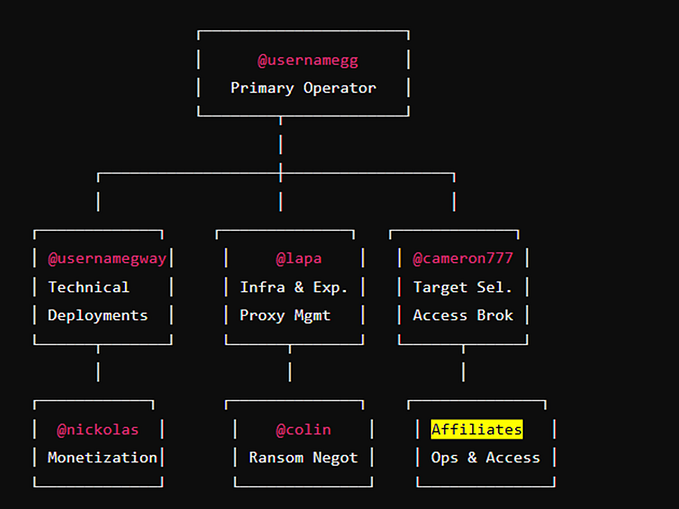
Member-only story
20 Simple Bug Bounty Automation Techniques
How to Automate Bug Hunting and Improve Efficiency in Bug Bounty Programs

Introduction: Why Automate Bug Bounty Hunting?
Bug bounty hunting can be time-consuming and repetitive, but automation can help you streamline reconnaissance, scanning, and exploitation tasks. By using automation, beginners can:
✅ Save time by reducing manual efforts
✅ Improve efficiency by running tools in the background
✅ Discover more vulnerabilities by scanning large targets quickly
✅ Focus on advanced exploitation instead of repetitive tasks
In this guide, we’ll explore 20 essential bug bounty automation techniques to help beginners speed up their workflow and maximize findings.
1. Automated Subdomain Enumeration
Finding subdomains is the first step in reconnaissance. Use tools like Subfinder, Amass, and Assetfinder to automate subdomain discovery.
subfinder -d target.com -o subdomains.txt
amass enum -passive -d target.com -o subdomains.txt
assetfinder --subs-only target.com >> subdomains.txt