Member-only story
Secure Hash Algorithm 1 (SHA-1): A Comprehensive Overview
Properties, Applications, and Vulnerabilities of SHA-1 | Karthikeyan Nagaraj
5 min readMar 3, 2023
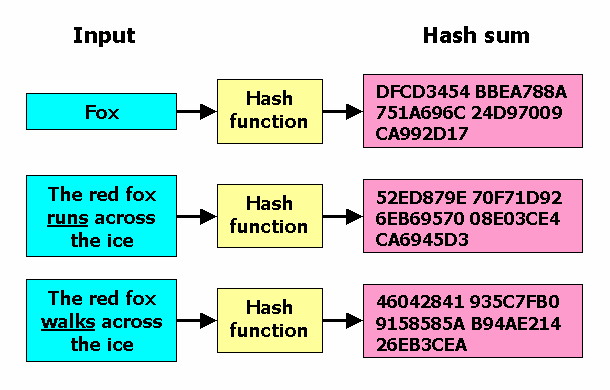
In the field of cybersecurity, hash algorithms play a crucial role in ensuring data integrity and confidentiality. Among various hash functions available today, one of the most widely used algorithms is the Secure Hash Algorithm 1 (SHA-1). In this article, we will delve deeper into SHA-1, its properties, applications, and vulnerabilities.
Introduction to SHA-1:
- SHA-1 is a cryptographic hash function that produces a 160-bit hash value (also known as a message digest) from an input message of any size, up to 2⁶⁴ — 1 bits.
- SHA-1 was designed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in 1995 as a part of the Secure Hash Standard (SHS).
- SHA-1 is a one-way function, which means it is computationally infeasible to derive the original message from its hash value.
Properties of SHA-1:
SHA-1 has several properties that make it suitable for various applications:
- Collision Resistance: The primary goal of a hash function is to produce a unique hash value for each input message. SHA-1 ensures that two different messages are highly unlikely to produce the same hash value, making it resistant to collision attacks.
- One-way Function: SHA-1 is a one-way function, which means it is impossible to derive the original message from its hash value. This property is essential in digital signatures, password storage, and other security applications.
- Fixed Output Length: SHA-1 produces a fixed-size output of 160 bits, regardless of the input message size. This makes it easy to compare hash values and store them in databases.
Applications of SHA-1:
SHA-1 is used in various applications, including:
- Digital Signatures: SHA-1 is used in digital signature algorithms such as Digital Signature Standard (DSS) to ensure data integrity and non-repudiation.
- Password Storage: SHA-1 is used to store…
